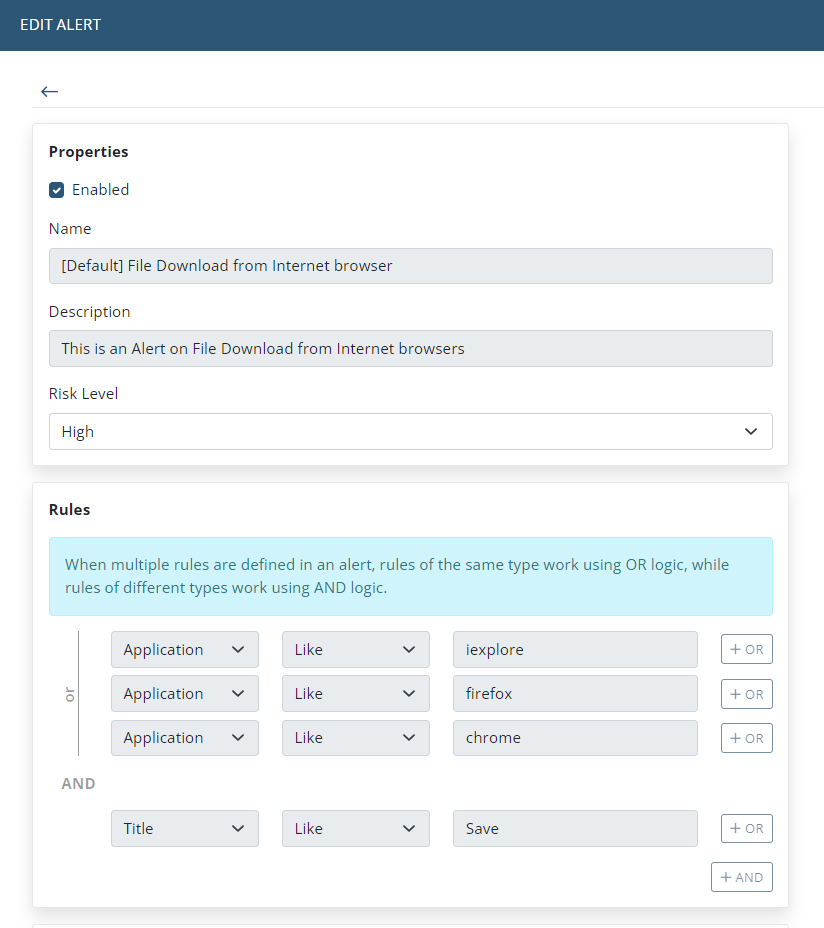
Alert Rules
Alert rules allow you to determine what events on the computers being investigated will be considered and detected as an alert, and therefore trigger the alert resulting in an alert event. Each alert must have at least one rule.
Each alert rule consists of the following (specified in the 3 fields in the Rules section, from left to right respectively):
• a parameter.
• a comparison operator.
• a value (to which the parameter will be compared).
Table of Contents
1. Parameters
The following parameter types can be selected to use for rules:
Parameter | Description | Example Value |
Parameters applied to all Clients | ||
Username | The value is the name of the user whose activity is to be monitored. Select this parameter type for the alert to be triggered whenever the specified user logs in to a Client computer. For Windows or macOS users, a domain name (or computer name for local Windows users) can also be used (i.e. specified before the username), by entering the value of the username in the following format: • For a Windows user: <domain name or computer name>\<username> • For a macOS user: <domain name>\<username> If secondary user authentication is enabled and the secondary user login username matches the username alert parameter, the alert is triggered. For example: The alert rule is defined as Username Like John, and the user logs in to (a Windows or Linux computer) as “Guest” and then enters “John” as the secondary login username. The alert is then triggered, and first record in the session of this user “(Guest (John))” is indicated as an alert event (e.g. in the Metadata grid in the Session Viewer). | John |
Parameters applied to Windows, macOS, and Linux Clients (for X Window System sessions only) | ||
Application | The value is the name of the application opened on the Client computers being investigated. Select this parameter type for the alert to be triggered whenever the specified value is identified as the name of an application opened. | skype.exe |
Title | The value is the name that appears in the title of a window. Select this parameter type for the alert to be triggered whenever the specified value is identified in any window title on the screen. | My document |
Parameters applied to Windows and macOS Clients only | ||
Keystrokes (Windows/macOS) | The value is the keystrokes entered by the user. Select this parameter type for the alert to be triggered whenever the specified value is entered. | download |
URL (Windows/macOS) | The value is the URL entered in the browser address bar or visited by the user. Select this parameter type for the alert to be triggered whenever the specified value is identified as the URL. NOTE: The URL monitoring option must be enabled for the Client. | facebook.com |
Clipboard Copy (Windows/macOS) | The value is the clipboard value copied or cut by the user. Select this parameter type for the alert to be triggered whenever the specified value is copied or cut. Enter an asterisk (*) in the value field if you want to detect any copying or cutting action. | confidential |
| Clipboard Paste (Windows/macOS) | The value is the clipboard value pasted by the user. Select this parameter type for the alert to be triggered whenever the specified value is pasted. Enter an asterisk (*) in the value field if you want to detect any pasting action. | confidential |
| File Upload (Windows/macOS) | The value is the filename of the file uploaded by the user. Select this parameter type for the alert to be triggered whenever a file with the specified filename is uploaded. NOTE: For Windows Clients, custom alerts can also be added to be triggered on file upload/download by combining multiple rules using the other alert rule parameter types, similar to, for example, the default alert on detecting file download from an Internet browser, which uses the following combination of four rules:
In this example, if any of the 3 browser applications (defined in the first 3 rules) are used, and a window is opened containing the word “Save” in its title (as defined in the fourth rule), then the alert will be triggered. See also Examples of Alert Rules. | * *.exe *.app c:\TopSecret\*.* [currently only available for Windows Clients] |
Parameters applied to Linux Clients only (both SSH and X Window System sessions) | ||
Command (Linux) | The value is the command entered in the Linux terminal. Select this parameter type for the alert to be triggered whenever the specified command is entered. | sudo |
Parameter (Linux) | The value is the Linux parameter entered. Select this parameter type for the alert to be triggered whenever the user enters a command along with the specified parameters. | ImportantDocument |
Parameters applied to Active Directory Groups (for Windows and macOS Clients only) | ||
| User Belonging to Domain Group (Windows/macOS) | The value is the name of the domain group. The comparison operator is the Active Directory domain name (instead of the usual comparison operators: Equals, like, Not equals, or Not like). Select this parameter type for an alert to be triggered whenever a user of the specified domain group starts to use (i.e. log in to) a Client computer. | Marketing |
| Parameters applied to Active Directory Groups (for Windows Clients only) | ||
Computer Belonging to Domain Group (Windows) | The value is the name of the domain group. The comparison operator is the Active Directory domain name (instead of the usual comparison operators: Equals, like, Not equals, or Not like). Select this parameter type for the alert to be triggered whenever a Client computer belonging to this domain group starts being used (i.e. a user logs in to it). NOTE: Alerts containing this parameter need to be assigned to the All Clients group to function correctly. | Accounting |
2. Comparison Operators
For all alert rule parameters except for parameters that belong to Active Directory groups, you can select the following comparison operators to use for rules:
Comparison Operator | Description | Example | ||
| Value | Found | Not Found | ||
Equals | The result found is an exact match to the defined value. | Jon | Jon | Jonnie |
Like | The result found contains the defined value. | Jon | Jonnie, Jonathan | Johan |
Not equals | The result found does not match the defined value. | Jon | Oliver, Jonnie | Jon |
Not like | The result found does not contain the defined value. | Jon | Oliver, Johan | Jon, Jonnie, Jonathan |
In additional to the comparison operators listed above, for most parameters, the Matches (Regex) comparison operator can also be used to define regular expressions (regex) in alert rules to trigger alerts on Windows Client computers.
3. Examples of Using Multiple Rules in an Alert
Rules defined with Windows and Linux parameters do not influence one another. Therefore, you can define multiple rules for both Windows and Linux Clients in a single alert, and the alert will work correctly.
For example:
Parameter | Comparison Operator | Value | |
Rule 1 | Command | Equals | su |
| Logical Operator | OR | ||
Rule 2 | URL | Like | facebook.com |
Result | The alert will be triggered by a user entering the “su” command in the Linux terminal, or by visiting the facebook.com website on a computer running the Windows operating system. | ||
Where multiple rules are defined with the same parameter using the OR logical operator in a single alert using Like or Equals comparison operators, the alert will be triggered if the conditions of at least one of the rules are met (i.e. using OR logic).
For example:
Parameter | Comparison Operator | Value | |
Rule 1 | Application | Equals | skype.exe |
| Logical Operator | OR | ||
Rule 2 | Application | Equals | winword.exe |
Result | The alert will be triggered by any user opening either the Skype or Microsoft Word applications. | ||
Where multiple rules are defined with different parameters using the AND logical operator in a single alert using Like or Equals comparison operators, the alert will only be triggered if the conditions of all the rules are met (i.e. using AND logic).
For example:
Parameter | Comparison Operator | Value | |
Rule 1 | Application | Equals | skype.exe |
| Logical Operator | AND | ||
Rule 2 | Username | Like | Nancy |
Result | The alert will be triggered by the user Nancy opening the Skype application. | ||
Where multiple rules are defined with one parameter using the OR logical operator and another rule is defined with a different parameter using the AND logical operator in a single alert using the Like or Equals comparison operators, the alert will be triggered if any of the conditions are met of any rule defined with the first parameter (using the OR logical operator), and the conditions are met for the rule defined with the different parameter (using the AND logical operator).
For example:
Parameter | Comparison Operator | Value | |
Rule 1 | Application | Equals | skype.exe |
| Logical Operator | OR | ||
Rule 2 | Application | Equals | winword.exe |
| Logical Operator | AND | ||
Rule 3 | Username | Equals | Nancy |
Result | The alert will by triggered by the user Nancy opening either Skype or Microsoft Word. | ||
Where multiple rules are defined with the same parameter using the AND logical operator in a single alert using the Not equals or Not like comparison operators, the alert will be triggered if the conditions are met for all of the rules defined.
For example:
Parameter | Comparison Operator | Value | |
Rule 1 | Application | Not equals | skype.exe |
| Logical Operator | AND | ||
Rule 2 | Application | Not equals | winword.exe |
Result | The alert will be triggered by any user opening any application except Skype and Microsoft Word. | ||