Syteca Encryption
Table of Contents
1. General Information
On the first startup, the Ekran System Application Server generates the Ekran System Master Certificate (EkranMasterCertificate) and saves it to the Certificates storage in Windows.
The Ekran System Master Certificate is a unique RSA-2048 certificate, without which Ekran System would not be able to receive other keys or read encrypted data.
If you need to move the database, you first need to back up the Ekran System Master Certificate, and then import or export it.
On the Application Server side, encryption is implemented using Microsoft .NET framework.
On the Client side, encryption is implemented using Crypto++.
All encryption algorithms use FIPS 140-2 certified encryption implementations.
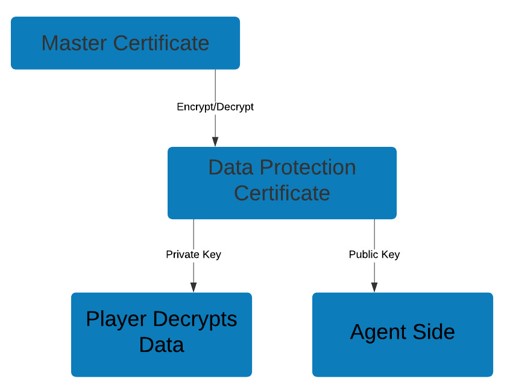
The Ekran System Master Certificate is used to encrypt the Ekran System Data Protection certificate, and the latter is stored in the database in encrypted form.
The Data Protection certificate is in turn used to encrypt the data stored in database, including binary data (i.e. screen captures).
The Data Protection certificate is an RSA-2048 certificate. This same public key is used by all Clients for encryption of their data. Its private key is not used by Clients, but is only used on the Application Server side to decrypt data.
2. Encryption of Monitoring Data
The Data Protection certificate’s public key is used to encrypt the binary data (i.e. the screen captures) as follows: For each fragment of binary data, an AES-256 Key / IV pair is generated which is used to encrypt the binary data. The pair itself is then also encrypted using the Data Protection certificate’s public key.
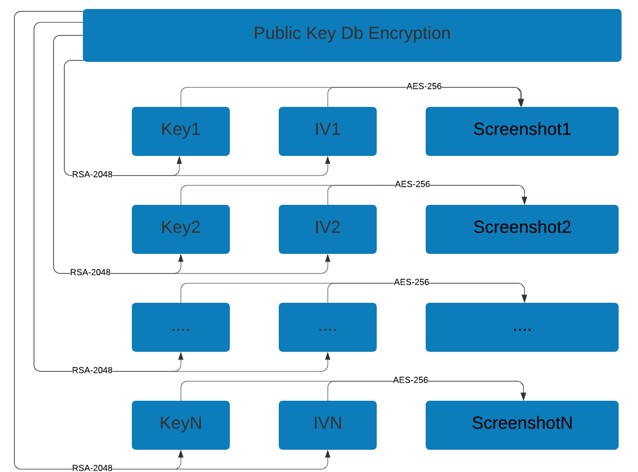
For the AES encryption algorithm, CTR mode is used.
NOTE: CTR mode is also known as integer counter mode (ICM) and segmented integer counter (SIC) mode.
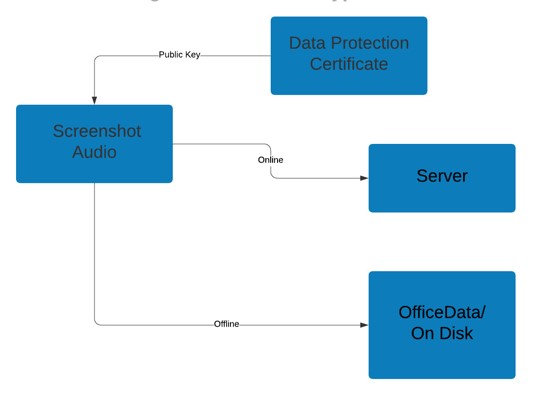
To decrypt the data, the AES key is first decrypted with the private key of the Ekran System Master Certificate, and then the original data is decrypted with the AES key. On the Client side, the data is encrypted during creation, and then decrypted by the Application Server when an authorized Ekran System user views it in the Management Tool.
Data in the offline pool is already stored in encrypted form, so no additional encryption is required.
Keystrokes logged are encrypted in the MS SQL database and the PostgreSQL database. The Symmetric key, which is stored in the database, is password-protected, and the password is encrypted with the Ekran System Master Certificate.
3. Encryption of Connections
Connections between Ekran System Clients and the Ekran System Application Server are encrypted with AES-256. The key generation is based on the Deffie-Hellman key exchange algorithm. Encryption is implemented using Crypto++ 5.6.1.
Connections between the Ekran System Application Server and the Management Tool establish TCP connections encrypted with a self-signed certificate. Encryption is implemented using WCF .NET.
Access to the Management Tool is established over an encrypted HTTPS connection. The certificate is defined before installation of the Management Tool. For more information, see the Using a Self-Signed Certificate section in the Ekran System User Manual.
The database connection string is stored in the registry. It is encrypted with the Ekran System Master Certificate.
Ekran System can also be configured to use SSL encryption for the connection between the Application Server and the database (for both MS SQL Server and PostgreSQL, including when using Amazon Web Services RDS for PostgreSQL).
4. Encryption of Other Data
The initial vectors for time-based one-time passwords (TOTP) are encrypted in the database using the Ekran System Master Certificate.
The passwords of Ekran System internal users are stored as SHA-256 hash values.
Secrets with credentials of privileged accounts are encrypted using AES-256.
The results of Forensic Export are encrypted using RSA-1024.
