System Components
Syteca is a software solution specially designed to manage privileged user access (PAM), as well as remotely monitor and control user activity (UAM) on endpoint Client machines.
Table of Contents
1. Main System Components
The system includes the following main software application components:
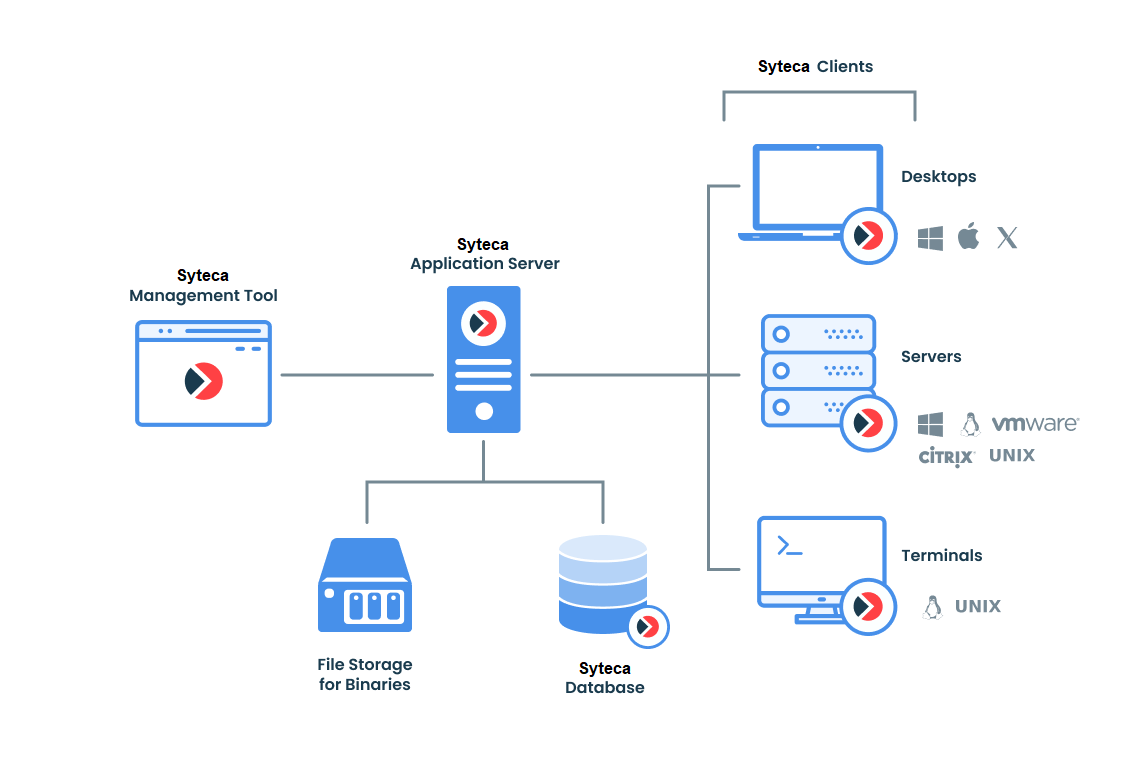
• NOT AVAILABLE IN SAAS Syteca Application Server (further referred to as the Application Server or the Server): This is the main component of Syteca which receives the monitored data (the screen captures and associated metadata) from Syteca Clients, analyses the data (and generates alerts to potential security incidents), and stores it in the central database (with the third-party MS SQL or PostgreSQL databases supported). The Application server is also responsible for storing the configuration data, sending the update packages to Clients, performing database cleanup, and creating reports and corresponding statistics. The operation of the Application Server can be started or stopped by way of the Server Tray icon, which also includes the Database Parameters (DbSetupToolUI) application where the Syteca Master Certificate can be reissued or moved, and the database parameters can be modified, etc.
• Syteca Management Tool (further referred to as the Management Tool): With a convenient web-based user interface, this is the central administrative console that allows you to view and analyze the monitored security data from Clients, as well as manage the Clients, users, USB monitoring rules, alerts, the database, serial keys, etc. You can access the Management Tool remotely using any computer in the network, without having to install it on that computer. The Management Tool includes the Session Viewer which provides a user-friendly interface for quick review of the monitored data received from Syteca Clients, including playing back in the form of video the screen captures recorded in any selected Client session.
• Syteca Clients (further referred to as Clients), installed on endpoints:
- Syteca Windows Clients (further referred to as Windows Clients): Being hosted on remote computers, Windows Clients record screen captures with mouse movements in the form of video at the defined frequency, and send them to the Application Server along with metadata such as user name, host name, activity times, active window titles, application names, URLs, clipboard text data, keystrokes, etc. Managing the configuration and settings of the remote Windows Clients is performed by using the Management Tool.
- Syteca macOS Clients (further referred to as macOS Clients): Being hosted on remote computers, macOS Clients record screen captures with mouse movements in the form of video at the defined frequency, and send them to the Application Server along with metadata such as user name, host name, activity times, active window titles, application names, etc. Managing the configuration and settings of the remote macOS Clients is performed by using the Management Tool.
- Syteca Linux/Unix Clients including X Window System (further referred to as Linux Clients): Being hosted on remote computers, Linux Clients capture input/output terminal data (including all commands executed), and send this interactive data to the Application Server.
• NOT AVAILABLE IN SAAS Syteca Tray Notifications application (further referred to as the Tray Notifications application): This application allows notifications to be received from Clients about alert events on them.
2. Other System Components
Other stand-alone software application components of Syteca can also be used:
• NOT AVAILABLE IN SAAS Syteca Master Panel (further referred to as the Master Panel): This additional stand-alone component of Syteca can be used for large-scale deployments in High-Availability mode, and combines the data from all the Syteca Applications Servers instances on different nodes, allowing all the Client sessions to be viewed in a single user interface.
• Syteca SDK (for developers): Syteca Software Development Kit consists of APIs and other tools, which allow developers to integrate Syteca with customers' information systems so as to facilitate the transfer of business intelligence (BI) and other data between them.
3. The Basic Deployment Scheme
Maximum visibility and control of any activity performed within an organization's infrastructure can be achieved by installing Clients of the corresponding type on each endpoint.